Category:Attack Categorisation By Attacker Model: Access to Valid Token and Certificate Injection: Difference between pages
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
=Introduction= | |||
=Attack subtypes= | |||
There are no attack subtypes for this attack. | |||
== | |||
=Prerequisites= | |||
=Target= | |||
[[File:Target_Session_Managment.jpg|centre|600px]] <br> | |||
The attacked Single Sign-On component is marked in red colour. <br> | |||
The attack uses the CSRF technique to enforce the victim to change changing configuration data without explicit user interaction. | |||
=Description= | |||
=Mitigation / Countermeasures= | |||
Session Management schould include a protection against CSRF to mitigate the attack. | |||
=Practical Examples= | |||
In 2014, Mainka et al. analyzed 22 Software as a Service cloud providers and found out, that different frameworks were vulnerable to this attack: | |||
SAManage, Shiftplanning, BambooHR, IdeaScale, Howlr and CA Service Management. | |||
=References= | |||
C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk (2014): Your Software at my Service: Security Analysis of SaaS Single Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security Workshop (CCSW). | |||
Revision as of 18:01, 2 February 2016
Introduction
Attack subtypes
There are no attack subtypes for this attack.
Prerequisites
Target
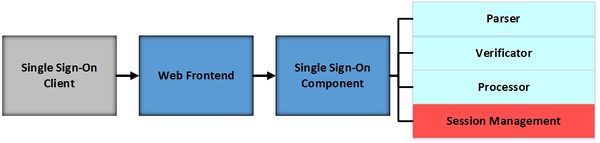
The attacked Single Sign-On component is marked in red colour.
The attack uses the CSRF technique to enforce the victim to change changing configuration data without explicit user interaction.
Description
Mitigation / Countermeasures
Session Management schould include a protection against CSRF to mitigate the attack.
Practical Examples
In 2014, Mainka et al. analyzed 22 Software as a Service cloud providers and found out, that different frameworks were vulnerable to this attack: SAManage, Shiftplanning, BambooHR, IdeaScale, Howlr and CA Service Management.
References
C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk (2014): Your Software at my Service: Security Analysis of SaaS Single Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security Workshop (CCSW).
Pages in category "Attack Categorisation By Attacker Model: Access to Valid Token"
The following 3 pages are in this category, out of 3 total.