Certificate Faking and Replay Attack: Difference between pages
(→Target) |
(→Target) |
||
| Line 1: | Line 1: | ||
=Introduction= | =Introduction= | ||
Every [https://en.wikipedia.org/wiki/Single_sign-on SSO] protocol provides freshness parameters ''N'' to limit the reuse and lifetime of the authentication tokens. Taking into account that the reuse of tokens is optional, the validation of the attributes providing freshness is not considered as critical. On the other hand, the time restriction regarding the usage of authentication tokens is more critical and should be evaluated. Otherwise, tokens issued once might be valid for an extended time period or even an infinite amount of time. | |||
The attack targets the | The attack specifically targets the SSO Verificator. | ||
=Attack subtypes= | =Attack subtypes= | ||
| Line 8: | Line 8: | ||
=Prerequisites= | =Prerequisites= | ||
The attacker needs access to a valid token. More specifically, the token in question is required to be valid for the ''Software-as-a-Service Cloud Provider (SaaS-CP)'' at any time in the past. This can be achieved if the attacker had legitimate access (for a limited period of time) to the ''SaaS-CP'' via ''SSO'' and used this access to generate and store a token for himself. Alternatively, searching for published tokens in forums or in technical documentations could also provide valid, though most possibly outdated, tokens. | |||
=Target= | =Target= | ||
| Line 15: | Line 15: | ||
=Description= | =Description= | ||
The | The attacker sends an expired authentication token to the target ''SaaS-CP''. In case, that the unlimited reuse of authentication tokens is applicable and the token is successfully verified, the attack is classified as successful. | ||
The attack’s impact is average since the attacker has limited attack surface – he can only spend authentication tokens he possesses. However, the potential impact drastically rises in case the attacker gains hold of an authentication token granting him extended access rights (e.g., as an administrator of the system). | |||
[[File:Replay_Attack.jpg]] | |||
<br> | |||
SAML token with expired timestamps is sent to the ''SaaS-CP''. | |||
=Mitigation / Countermeasures= | =Mitigation / Countermeasures= | ||
This | This component should validate attributes providing the corresponding restrictions, i.e., the freshness parameter ''N''. In the SAML context relevant to this study, this parameter is represented by ''NotOnOrAfter'' and ''NotBefore''. Failing to | ||
properly verify these parameters will enable this attack type. Another possibility to enable this attack type would be via additional freshness attributes, which are not part of the digital signature ''s''. | |||
=Practical Examples= | =Practical Examples= | ||
In 2014, Mainka et al. analyzed 22 Software as a Service cloud providers and found out, that different frameworks were vulnerable to this attack: Clarizen, Instructure, AppDynamics, TimeOffManager, LiveHive and CA Service Management. | |||
[[Category:Attack_Categorisation_By_Attacker_Model: | [[Category:Attack_Categorisation_By_Attacker_Model:_Access_to_Valid_Token]] | ||
[[Category:Attack_Categorisation_By_Violated_Security_Objective_Access_Control]] | [[Category:Attack_Categorisation_By_Violated_Security_Objective_Access_Control]] | ||
[[Category:Attack_Categorisation_By_Attack_on_IdP/_SP:_Attack_on_SP]] | [[Category:Attack_Categorisation_By_Attack_on_IdP/_SP:_Attack_on_SP]] | ||
[[Category:Attack_Categorisation_By_Attacked_Web_Service_Component:_Signature_Verification]] | [[Category:Attack_Categorisation_By_Attacked_Web_Service_Component:_Signature_Verification]] | ||
[[Category:Attack_Categorisation_By_Attack_Spreading: | [[Category:Attack_Categorisation_By_Attack_Spreading:Application_Specific_Flaws]] | ||
[[Category:Attack_Categorisation_By_Attack_on_SAML]] | [[Category:Attack_Categorisation_By_Attack_on_SAML]] | ||
=References= | =References= | ||
C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk | C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk (2014): Your Software at my Service: Security Analysis of SaaS Single Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security Workshop (CCSW). | ||
(2014): Your Software at my Service: Security Analysis of SaaS Single | |||
Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security | |||
Workshop (CCSW). | |||
Revision as of 18:25, 25 January 2016
Introduction
Every SSO protocol provides freshness parameters N to limit the reuse and lifetime of the authentication tokens. Taking into account that the reuse of tokens is optional, the validation of the attributes providing freshness is not considered as critical. On the other hand, the time restriction regarding the usage of authentication tokens is more critical and should be evaluated. Otherwise, tokens issued once might be valid for an extended time period or even an infinite amount of time.
The attack specifically targets the SSO Verificator.
Attack subtypes
There are no attack subtypes for this attack.
Prerequisites
The attacker needs access to a valid token. More specifically, the token in question is required to be valid for the Software-as-a-Service Cloud Provider (SaaS-CP) at any time in the past. This can be achieved if the attacker had legitimate access (for a limited period of time) to the SaaS-CP via SSO and used this access to generate and store a token for himself. Alternatively, searching for published tokens in forums or in technical documentations could also provide valid, though most possibly outdated, tokens.
Target
The attacked Single Sign-On component is marked in red colour.
Description
The attacker sends an expired authentication token to the target SaaS-CP. In case, that the unlimited reuse of authentication tokens is applicable and the token is successfully verified, the attack is classified as successful. The attack’s impact is average since the attacker has limited attack surface – he can only spend authentication tokens he possesses. However, the potential impact drastically rises in case the attacker gains hold of an authentication token granting him extended access rights (e.g., as an administrator of the system).
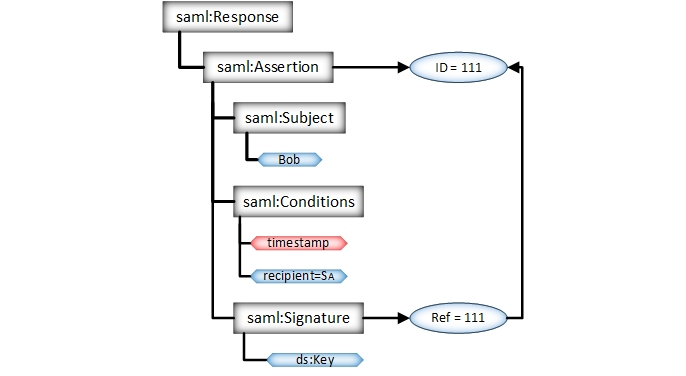
SAML token with expired timestamps is sent to the SaaS-CP.
Mitigation / Countermeasures
This component should validate attributes providing the corresponding restrictions, i.e., the freshness parameter N. In the SAML context relevant to this study, this parameter is represented by NotOnOrAfter and NotBefore. Failing to properly verify these parameters will enable this attack type. Another possibility to enable this attack type would be via additional freshness attributes, which are not part of the digital signature s.
Practical Examples
In 2014, Mainka et al. analyzed 22 Software as a Service cloud providers and found out, that different frameworks were vulnerable to this attack: Clarizen, Instructure, AppDynamics, TimeOffManager, LiveHive and CA Service Management.
References
C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk (2014): Your Software at my Service: Security Analysis of SaaS Single Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security Workshop (CCSW).
- Pages with broken file links
- Attack Categorisation By Attacker Model: Access to Valid Token
- Attack Categorisation By Violated Security Objective Access Control
- Attack Categorisation By Attack on IdP/ SP: Attack on SP
- Attack Categorisation By Attacked Web Service Component: Signature Verification
- Attack Categorisation By Attack Spreading:Application Specific Flaws
- Attack Categorisation By Attack on SAML